 |
| Disturbing Adware |
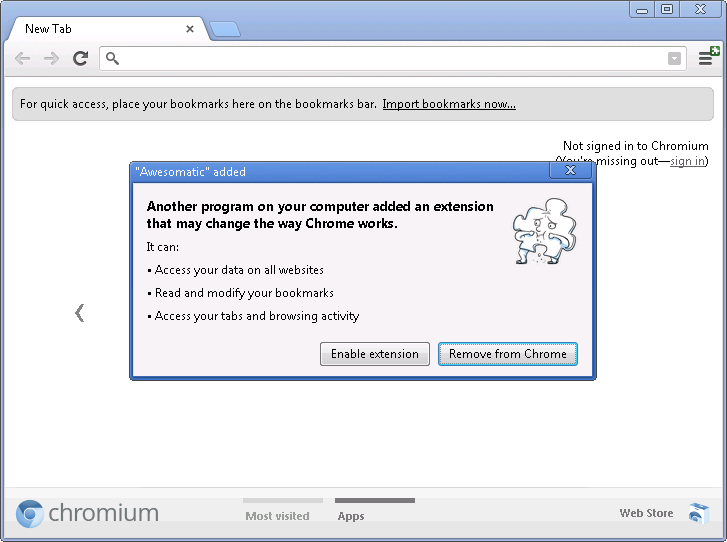
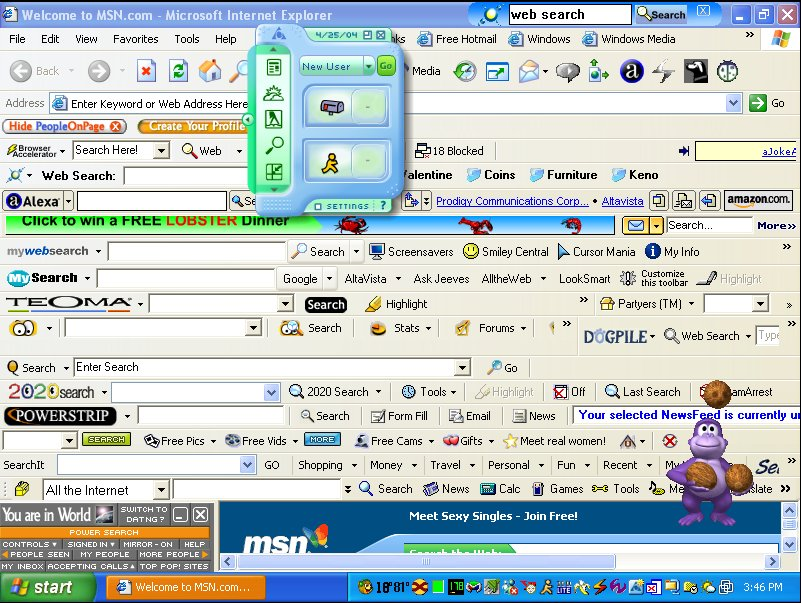
Recently emerging unwanted toolbars appear in your web browser. Do you often find your default search engine changed to a search engine that is unfamiliar? It is an attack of adware (advertisement attack) that originated from the application installation mistake on your computer. Most providers download a free application that is in the top rank in Google is working with advertising companies to try to trick you also install the toolbar, addons, or other forms of advertisement in your browser. As usual, you will hit next, next and next to install an application on your computer, and you have been unconsciously install adware which will also interfere with your daily activities a day using your browser.
This simple article will give you an easiest way to remove all Adware in all of your browsers (Firefox, Chrome, IE, Opera, etc.) with only 2 clicks.
Check out simple tutorial below :
- Download adware remover HERE !!
- Turn off all current browsers
- Open AdwCleaner, click Search then wait Search process complete
- Click Delete, and reboot your computer after the deleting process is completed.
- Cheer, your browser has been cleaned up.
The following is an adware that could be removed by this simple program :
- Remove Absolute Uninstaller - Ask Toolbar
- Remove Ad-ware - Google Chrome
- Remove Anvir Task Manager Free - Dealio Toolbar
- Remove Any Video Converter - Google Chrome
- Remove AVG Free - Yahoo Toolbar
- Remove AVG Linkscanner - Yahoo Toolbar
- Remove Conduit Toolbar
- Remove Bitcomet - Google Toolbar
- Remove BitTorrent - Ask Toolbar
- Remove BS.Player - BS. ControlBar
- Remove Burn4free - 1Click DVD Copy Pro
- Remove BurnAware Free - Ask Toolbar
- Remove CDBurnerXP - OpenCandy
- Remove Clamwin - Ask Toolbar
- Remove COMODO Internet Security - Ask Toolbar
- Remove Core Temp - Search Enhancement
- Remove Darkwave Studio - OpenCandy
- Remove Defraggler - Google Toolbar
- Remove Driver Sweeper - OpenCandy
- Remove ExtractNow - Registry Reviver
- Remove Flashget - Google Toolbar
- Remove FLVPlayer4Free - Video Download Toolbar
- Remove Free Commander - eBay Shortcuts
- Remove Facemoods Toolbar
- Remove HwMonitor
- Remove ICQ - ICQ Toolbar
- Remove IE7Pro - Grab Pro Toolbar
- Remove ImgBurn - Ask Toolbar
- Remove Immunet - Ask Toolbar
- Remove IObit SmartDefrag - IObit Toolbar
- Remove IrfanView - Google Toolbar
- Remove MediaCoder - Nitro PDF Reader
- Remove MediaInfo - OpenCandy
- Remove µTorrent - µTorrent toolbar
- Remove Orbit Downloader - Grab Pro
- Remove PC Tools Spyware Doctor - Google Toolbar
- Remove PC Wizard - Ask Toolbar
- Remove PicPick - Bing Toolbar
- Remove Recuva - Yahoo Toolbar
- Remove Spyware Terminator - Web Security Guard
- Remove Webshot - OpenCandy
- and Remove other suspicous malware / adware on your registry.